security fail: home DVR/camera systems
Many people, such as myself, decide to invest in home security camera systems. Most of them nowadays allow you connect directly to the system via your smartphone. As I am in the computer security field, I tend to wonder just how secure things are in my own home. So I put my NiteOwl 16 channel DVR system to the Pepsi challenge. It failed horribly.
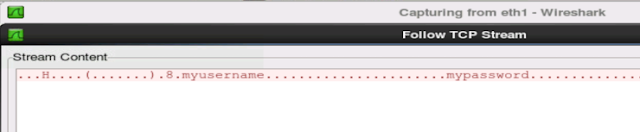
Whenever I send my username and password across the internet to look at my home security cameras, the credentials are sent in clear text. Anyone in computer security knows is a not a good thing. Clear-text credentials are very easy to intercept. And most people don't know how to properly defend themselves and their home against cyber threats. So lots of people will use one password for everything. So if someone was to intercept this DVR password, the attacker has a lot of helpful information.
The intercepted information will include:
NiteOwl - failed
Zmodo - failed
A-See Pro - failed
Q-See: no credentials passed at first, but I can't be sure it never will since I don't have the DVR to make a valid connection. Chances are the exchange happens after the javascript file is executed. If I can find someone with a Q-See system, I should be able to properly verify.
Samsung: At first it looked ok since unlike the others, it was not sending clear text passwords up front.
But then i noticed it was providing a field called "Authorization" and a value that looked like a base64 code. So i took the code to my favorite web site for decoding base64
And there is our username/password. Weak security, but better than nothing compared to the others.

Defender: same thing as Samsung, just base64
Lorex - failed

still testing a few more, but so far I am not impressed by any of them.
My advice for now, if you have one of these systems, make sure the password you use to connect to the system is a password you do NOT use for anything else. Also make sure the cameras are not recording anything sensitive. If they are, I recommend disconnecting the DVR from the internet.
Whenever I send my username and password across the internet to look at my home security cameras, the credentials are sent in clear text. Anyone in computer security knows is a not a good thing. Clear-text credentials are very easy to intercept. And most people don't know how to properly defend themselves and their home against cyber threats. So lots of people will use one password for everything. So if someone was to intercept this DVR password, the attacker has a lot of helpful information.
The intercepted information will include:
- the username, which is likely the username also used in at least one of the computers on the victim's home network.
- the username's password, which is also likely to be the same password on the computer mentioned above
- the destination IP address, which tells the attacker where you are and what to attack.
Given how many people use the same password for everything and leave their home network devices on the default settings, sending a clear-text password can be a recipe for disaster. So let's see which home security DVR systems failed the test.
NiteOwl - failed

Zmodo - failed
A-See Pro - failed
Q-See: no credentials passed at first, but I can't be sure it never will since I don't have the DVR to make a valid connection. Chances are the exchange happens after the javascript file is executed. If I can find someone with a Q-See system, I should be able to properly verify.
Samsung: At first it looked ok since unlike the others, it was not sending clear text passwords up front.
But then i noticed it was providing a field called "Authorization" and a value that looked like a base64 code. So i took the code to my favorite web site for decoding base64
And there is our username/password. Weak security, but better than nothing compared to the others.

Defender: same thing as Samsung, just base64
Lorex - failed
Swann - failed

still testing a few more, but so far I am not impressed by any of them.
My advice for now, if you have one of these systems, make sure the password you use to connect to the system is a password you do NOT use for anything else. Also make sure the cameras are not recording anything sensitive. If they are, I recommend disconnecting the DVR from the internet.







Comments
Post a Comment