security fail: home DVR/camera systems
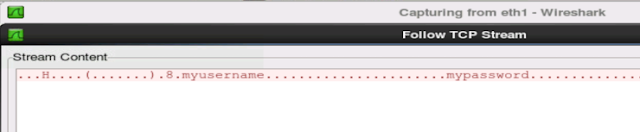
Many people, such as myself, decide to invest in home security camera systems. Most of them nowadays allow you connect directly to the system via your smartphone. As I am in the computer security field, I tend to wonder just how secure things are in my own home. So I put my NiteOwl 16 channel DVR system to the Pepsi challenge. It failed horribly. Whenever I send my username and password across the internet to look at my home security cameras, the credentials are sent in clear text. Anyone in computer security knows is a not a good thing. Clear-text credentials are very easy to intercept. And most people don't know how to properly defend themselves and their home against cyber threats. So lots of people will use one password for everything. So if someone was to intercept this DVR password, the attacker has a lot of helpful information. The intercepted information will include: the username, which is likely the username also used in at least one of the computers on t
